TheDeveloperBlog.com
C-Sharp | Java | Python | Swift | GO | WPF | Ruby | Scala | F# | JavaScript | SQL | PHP | Angular | HTML
DBMS Static Hashing
DBMS Static Hashing with DBMS Overview, DBMS vs Files System, DBMS Architecture, Three schema Architecture, DBMS Language, DBMS Keys, DBMS Generalization, DBMS Specialization, Relational Model concept, SQL Introduction, Advantage of SQL, DBMS Normalization, Functional Dependency, DBMS Schedule, Concurrency Control etc.
Static HashingIn static hashing, the resultant data bucket address will always be the same. That means if we generate an address for EMP_ID =103 using the hash function mod (5) then it will always result in same bucket address 3. Here, there will be no change in the bucket address. Hence in this static hashing, the number of data buckets in memory remains constant throughout. In this example, we will have five data buckets in the memory used to store the data. 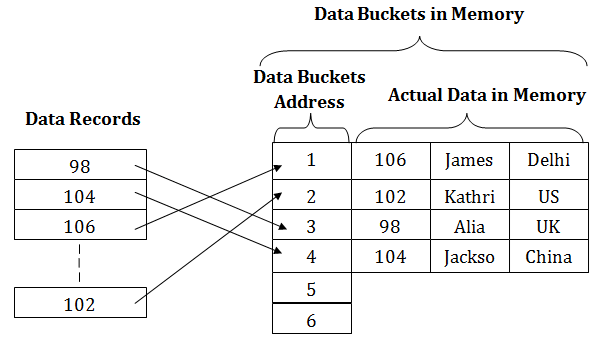
Operations of Static Hashing
When a record needs to be searched, then the same hash function retrieves the address of the bucket where the data is stored.
When a new record is inserted into the table, then we will generate an address for a new record based on the hash key and record is stored in that location.
To delete a record, we will first fetch the record which is supposed to be deleted. Then we will delete the records for that address in memory.
To update a record, we will first search it using a hash function, and then the data record is updated. If we want to insert some new record into the file but the address of a data bucket generated by the hash function is not empty, or data already exists in that address. This situation in the static hashing is known as bucket overflow. This is a critical situation in this method. To overcome this situation, there are various methods. Some commonly used methods are as follows: 1. Open Hashing
When a hash function generates an address at which data is already stored, then the next bucket will be allocated to it. This mechanism is called as Linear Probing. For example: suppose R3 is a new address which needs to be inserted, the hash function generates address as 112 for R3. But the generated address is already full. So the system searches next available data bucket, 113 and assigns R3 to it. 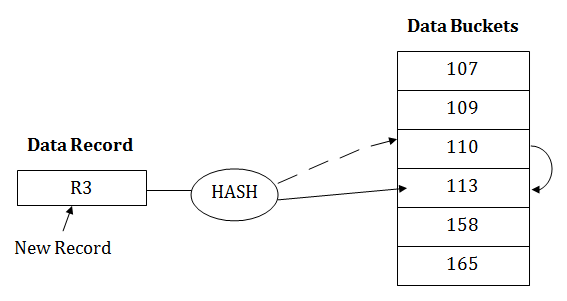
2. Close Hashing
When buckets are full, then a new data bucket is allocated for the same hash result and is linked after the previous one. This mechanism is known as Overflow chaining. For example: Suppose R3 is a new address which needs to be inserted into the table, the hash function generates address as 110 for it. But this bucket is full to store the new data. In this case, a new bucket is inserted at the end of 110 buckets and is linked to it. 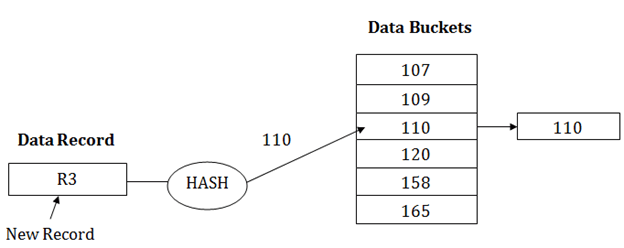
Next TopicDynamic Hashing
|
Related Links:
- DBMS Multivalued Dependency
- DBMS Inclusion Dependence
- DBMS SQL Set Operation
- Top 52 DBMS Interview Questions (2021)
- DBMS Transaction Processing Concept
- DBMS States of Transaction
- DBMS Schedule
- DBMS Conflict Serializable Schedule
- DBMS View Serializability
- DBMS Recoverability of Schedule
- DBMS Tutorial | Database Management System
- DBMS Failure Classification
- DBMS Concurrency Control
- DBMS Lock based Protocol
- DBMS Log-Based Recovery
- DBMS Checkpoint
- DBMS Timestamp Ordering Protocol
- DBMS Validation based Protocol
- DBMS Thomas Write Rule
- DBMS Multiple Granularity
- DBMS Sequential File Organization
- DBMS Recovery Concurrent Transaction
- DBMS Characteristics of SQL
- DBMS File organization
- DBMS Heap File Organization
- DBMS Hash File Organization
- DBMS B+ Tree
- DBMS RAID
- DBMS B+ File Organization
- DBMS Indexed Sequential Access Method
- DBMS Cluster File Organization
- DBMS Hashing
- DBMS Static Hashing
- DBMS Dynamic Hashing
- DBMS SQL Introduction
- DBMS Advantage of SQL
- SQL Commands: DDL, DML, DCL, TCL, DQL
- DBMS SQL Operator
- DBMS SQL Insert
- DBMS SQL Update
- DBMS SQl Datatype
- DBMS SQL Table
- DBMS SQL Select
- DBMS SQL Index
- DBMS SQL Sub Queries
- DBMS SQL Clauses
- DBMS Generalization
- DBMS Specialization
- DBMS vs Files System
- DBMS Architecture
- DBMS SQL Delete
- DBMS SQL View
- DBMS Three schema Architecture
- DBMS Data model schema and Instance
- DBMS Join Operation
- DBMS Notation for ER diagram
- DBMS Relational Calculus
- DBMS Data Independence
- DBMS Language
- DBMS ER model concept
- DBMS Mapping constraints
- DBMS Keys: Primary, Foreign, Candidate and Super Key
- DBMS Aggregation
- DBMS Join Dependency
- DBMS Convert ER into table
- DBMS Relationship of Higher Degree
- DBMS Relational Model concept
- DBMS Relational Algebra
- DBMS Integrity Constraints
- DBMS Functional Dependency
- DBMS Inference Rule
- DBMS Normalization: 1NF, 2NF, 3NF and BCNF with Examples
- DBMS Transaction Property
- DBMS Testing of Serializability
- DBMS 1NF
- DBMS 2NF
- DBMS SQL Aggregate function
- DBMS SQL Joins
- DBMS 3NF
- DBMS BCNF
- DBMS 4NF
- DBMS 5NF
- DBMS Relational Decomposition


